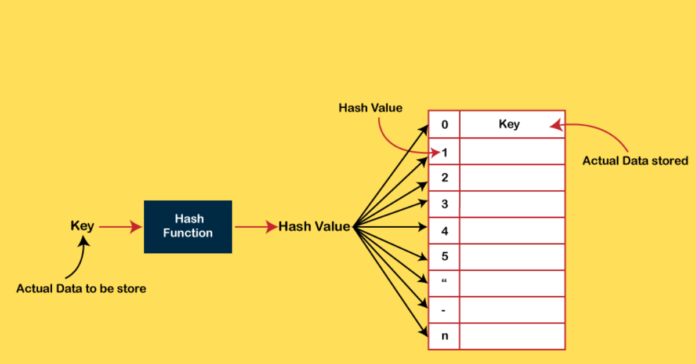
In computer science and information administration, hashing is essential, empowering adequate capacity, recovery, and information control. Let’s dive into the complexities of hashing, investigating its noteworthiness, components, preferences, applications, and more.
Demystifying Hashing
What is Hashing?
Hashing involves changing the input of variable measure over a fixed-size yield through numerical capacities known as hash capacities. These capacities relegate an exciting file or area for the information capacity inside an information structure.
Require for Hash Information Structure
The exponential development of information on the web requires viable capacity and recovery instruments. Whereas clusters serve as common information structures, their wastefulness in looking at massive datasets requires a more optimized arrangement – hashing.
Components of Hashing
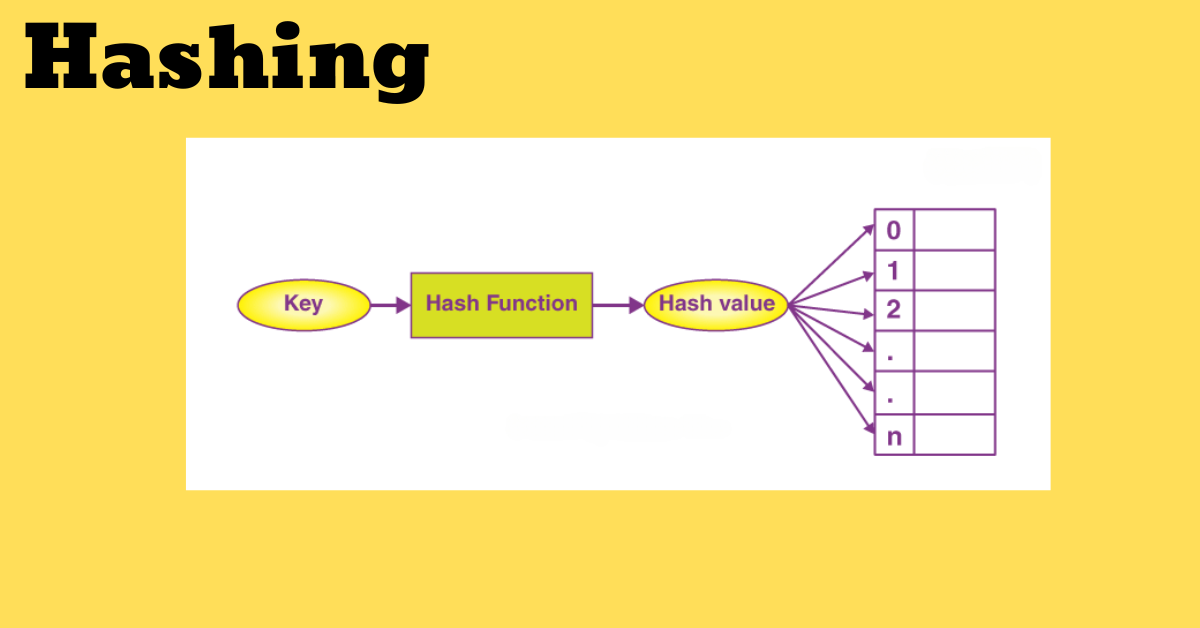
Key
A key, whether string or number, serves as the input for the hash work, deciding the capacity record inside the information structure.
Hash Function
The hash work forms the input key and produces a hash file, encouraging information capacity and recovery inside a hash table.
Hash Table
A hash table is a holder for information capacity, mapping keys to their comparing values utilizing the hash function.
Tending to Collisions
Collision
Collisions happen when particular keys deliver the same hash esteem, requiring collision taking care of procedures to oversee such scenarios viably. Different strategies, such as partitioned chaining or open tending, can be utilized to resolve collisions.
Focal Points of Hashing in Information Structures
Key-Value Support
Hashing exceeds expectations in executing key-value information structures and advertising productive mapping capabilities for putting away and recovering related values.
Quick Information Retrieval
With constant-time complexity, hashing empowers quick get to components inside the information structure, notwithstanding the measure of the dataset.
Efficiency
Including, cancelling, and looking are profoundly compelling with hashing methods, making it a perfect choice for overseeing energetic datasets.
Memory Utilization Reduction
Hashing optimizes memory utilization by distributing settled space for component capacity, lessening overhead, and upgrading general performance.
Scalability
Hashing shows fabulous adaptability, keeping consistent get-to-time with massive datasets, making it appropriate for applications with advancing information requirements.
Security and Encryption
Critical for secure information capacity and judgment confirmation, hashing is imperative in guaranteeing information security. It shapes the premise for cryptographic applications such as computerized marks, watchword hashing, and information keenness checks.
Applications of Hashing
Information Keenness Verification
Hashing is broadly utilized to guarantee the astuteness of information amid transmission or capacity. By producing exciting hash esteem for a dataset, any change can be recognized by comparing the hash esteem sometime recently and after the transmission/storage process.
Secret word Storage
In cybersecurity, hashing is utilized to store passwords safely. When putting away plaintext passwords, frameworks store their hashed values. Amid confirmation, the hashed watchword the client gives is compared with the put-away hash esteem, guaranteeing secrecy and securing against unauthorized access.
Cryptographic Applications
Hashing shapes the spine of different cryptographic conventions and calculations. From computerized marks to blockchain innovation, hashing plays an urgent part in guaranteeing information security, protection, and genuineness in computerized exchanges and communications.
Conclusion
In conclusion, hashing is a foundation in advanced information administration and security, advertising unparalleled effectiveness, adaptability, and unwavering quality. Understanding its components, preferences, and applications is vital for leveraging its full potential in assorted spaces, extending from computer program improvement to cybersecurity.
Frequently Inquired Questions
What are hash functions?
Hash capacities are numerical calculations that change over input information into fixed-size values, encouraging adequate information capacity and retrieval.
How does hashing upgrade information recovery speed?
By doling out one-of-a-kind files to information components, hashing empowers constant time to get to, making strides in recovery speed.
What challenges do collisions pose in hashing?
Collisions happen when diverse keys create the same hash esteem, requiring collision determination methods to guarantee information integrity.
Can hashing be utilized for encryption purposes?
Yes, hashing is fundamental for cryptographic applications, guaranteeing information security and judgment through procedures like computerized marks and secret word hashing.
Where can I learn more about hashing and its applications?
Explore comprehensive instructional exercises and courses on information structures and calculations to develop your understanding of hashing and its assorted applications.
“The DSA course made a difference in clearing the meet rounds for me. It was truly exceptionally supportive in setting a solid establishment for my problem-solving aptitudes. Truly awesome speculation, the enthusiasm Sandeep sir has towards DSA/teaching is what made the colossal contrast.” – Gaurav | Set at Amazon
Before you set out on your journey to improvement, ace the basics of DSA to construct a strong foundation for handling progressed calculations. Select your favored dialect and begin learning nowadays: