In this modern digital world, where everything is digitally connected, it is necessary to ensure that your operating system is secure to ensure your data, privacy, and digital safety. The following article will examine the basic steps and best practices for securing your operating system by preventing vulnerabilities and cyber threats.
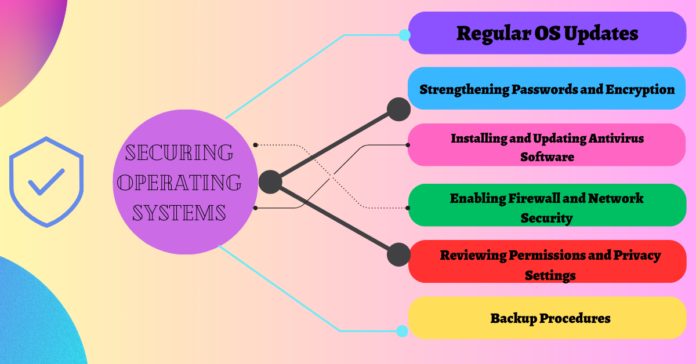
Regular OS Updates
Regularly updating your operating system is akin to fortifying the walls of your digital fortress. Vendors like Microsoft, Apple, or Linux distributions provide operating system updates and contain critical patches, bug fixes, and security enhancements. By keeping your OS up-to-date, you not only ensure the stability and performance of your system but also shield it against known vulnerabilities that malicious actors may exploit. Most modern operating systems offer the option for automatic updates, simplifying the process of staying protected.
Strengthening Passwords and Encryption
Passwords are the first defence against unauthorized access to your system and data. However, a weak or easily guessable password can render even the most robust security measures futile. To bolster your system’s security, adopt a password strategy emphasizing complexity and uniqueness. A strong password typically includes uppercase and lowercase letters, numbers, and special characters. Additionally, consider employing passphrase-based authentication for added resilience. Furthermore, encryption is pivotal in safeguarding sensitive data from prying eyes. Encrypting your hard drive, individual files, and communications ensures that the data remains unintelligible to the intruder, even if unauthorized access occurs.
Installing and Updating Antivirus Software
Antivirus software serves as a stalwart guardian in the ever-evolving landscape of cyber threats, continuously monitoring your system for malicious activity. These software solutions employ sophisticated algorithms to detect and neutralize various malware, including viruses, trojans, worms, and ransomware. However, the efficacy of antivirus software hinges on timely updates. New malware variants emerge regularly, necessitating frequent updates to antivirus databases and detection algorithms. Ensuring your antivirus software is up-to-date enhances your system’s resilience against emerging threats and bolsters its overall security posture.
Enabling Firewall and Network Security
A firewall acts as a digital sentry, scrutinizing incoming and outgoing network traffic and discerning between legitimate communication and potential threats. By configuring your firewall to block unauthorized access attempts and suspicious connections, you create a robust barrier against external threats. Additionally, implementing network security measures such as using secure Wi-Fi networks, turning off unnecessary services, and avoiding untrusted networks fortifies your system’s defences. Vigilance is key, as cybercriminals continually devise new tactics to circumvent security measures.
Reviewing Permissions and Privacy Settings
Your operating system and installed applications often request various permissions to access sensitive data and resources. While these permissions enable functionality, they pose potential security risks if granted indiscriminately. Regularly auditing permissions and privacy settings allows you to fine-tune access controls, granting only the necessary privileges to trusted applications and services. Moreover, configuring privacy settings to limit data collection and sharing mitigates the risk of accidental exposure to sensitive information.
Backup Procedures
Despite the best security measures, every system is impervious to data loss incidents. Hardware failures, malware infections, or human error can result in the irretrievable loss of critical data. Implementing robust backup procedures is essential to mitigate the impact of such incidents and facilitate swift recovery. Regularly backing up your data to external storage devices, cloud services, or network-attached storage ensures that your valuable data remains intact even during a catastrophic failure. Moreover, periodic backup integrity and redundancy testing further enhances your backup solution’s reliability.
Additional Considerations
In addition to the fundamental security measures outlined above, several additional considerations can bolster your operating system’s security posture:
- User Education: Educating users about cybersecurity best practices, such as avoiding suspicious links and emails, practicing safe browsing habits, and recognizing social engineering attempts, can significantly mitigate the risk of successful cyber attacks.
- Multi-Factor Authentication (MFA): Implementing MFA adds a layer of security to user accounts by requiring additional verification beyond passwords, such as biometric authentication or one-time codes.
- Software Restriction Policies: Employing software restriction policies or application whitelisting can prevent unauthorized or potentially malicious software from executing on your system, reducing the attack surface and enhancing security.
- Continuous Monitoring and Incident Response: Adopting a proactive approach to security involves monitoring system activity for signs of compromise or suspicious behaviour. Establishing robust incident response procedures enables swift detection, containment, and remediation of security incidents, minimizing their impact on your organization.
Last Idea
Securing your operating system is an ongoing endeavour that requires diligence, vigilance, and a proactive approach to cybersecurity. By implementing the essential steps outlined in this article and remaining abreast of emerging threats and best practices, you can fortify your system against potential vulnerabilities and safeguard your digital assets.
FAQs
Why are regular OS updates important?
- Regular OS updates patch security vulnerabilities and enhance system defences against emerging threats, bolstering overall security.
What constitutes a strong password?
- A strong password comprises a mix of uppercase and lowercase letters, numbers, and special characters, is unique, and avoids easily guessable patterns.
How often should antivirus software be updated?
- Antivirus software should be updated regularly, ideally configured for automatic updates, to ensure it remains effective against evolving threats.
What are the benefits of enabling a firewall?
- Enabling a firewall helps monitor and filter network traffic, blocking unauthorized access attempts and mitigating potential security risks.
Why is backing up data important?
- Backing up data is essential for mitigating the impact of data loss scenarios, enabling swift recovery in case of system compromises or failures.
What are some additional security measures to consider?
- Additional security measures include user education, multi-factor authentication, software restriction policies, continuous monitoring, and incident response.