In an age where digital connectivity dominates, ensuring the security of software applications has become paramount. The rise of sophisticated hackers and the ever-evolving landscape of cyber threats necessitate a proactive approach to software development. Enter the Principles of Secure Software Development—guidelines designed to fortify applications against malicious attacks and vulnerabilities.
Security by Design: A Proactive Approach
Gone are the days when security was an afterthought in software development. Today, organizations must adopt a proactive stance, integrating security measures into every development lifecycle phase. This proactive approach, Security by Design, emphasizes building resilience from the ground up.
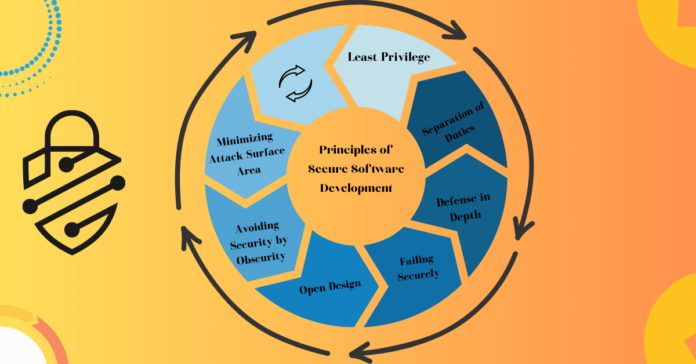
Principle 1: Least Privilege
The Principle of Least Privilege advocates granting individuals only the permissions necessary to perform their roles. By limiting access to sensitive information and functionalities, organizations can minimize the potential damage caused by a security breach.
Principle 2: Separation of Duties
Building upon the Principle of Least Privilege, the Principle of Separation of Duties ensures that no single individual possesses excessive authority. By distributing responsibilities among multiple roles, organizations mitigate the risk of insider threats and conflicts of interest.
Principle 3: Defense in Depth
Defence in Depth operates under the assumption that no single security measure is foolproof. Organizations can create a robust security posture capable of withstanding diverse threats by implementing multiple layers of defence, including physical, technical, and procedural safeguards.
Principle 4: Failing Securely
Inevitably, systems will encounter failures. The Principle of Failing Securely advocates designing systems that gracefully handle failures without compromising security. By implementing fail-safe mechanisms, organizations prevent unauthorized access and minimize the impact of potential breaches.
Principle 5: Open Design
The Principle of Open Design promotes transparency and scrutiny in software development. By openly sharing designs and implementations, organizations facilitate peer review and identify potential security flaws before malicious actors can exploit them.
Principle 6: Avoiding Security by Obscurity
Security by Obscurity—relying on secrecy to protect sensitive information—is inherently flawed. Instead, organizations should adopt transparent security practices, such as robust encryption and access controls, to safeguard their assets effectively.
Principle 7: Minimizing Attack Surface Area
Every feature and functionality in an application represents a potential entry point for attackers. The Principle of Minimizing Attack Surface Area advocates for reducing the complexity and exposure of applications to limit the opportunities for exploitation.
Embracing Secure Software Development

Incorporating the Principles of Secure Software Development into the development process is prudent and essential in today’s threat landscape. By adhering to these principles, organizations can build resilient applications that protect sensitive data, preserve operational integrity, and inspire user trust.
Going Deeper: Continuous Learning and Improvement
While understanding the core principles is crucial, mastering secure software development requires ongoing education and vigilance. Organizations can further enhance their security posture by investing in specialized training and adopting best practices recommended by industry experts.
conclusion
The principles of Secure Software Development provide a framework for building resilient applications in an increasingly interconnected world. Organizations can mitigate risks, thwart attacks, and safeguard their digital assets effectively by prioritizing security from inception to deployment. In an era of cyber threats, proactive security measures are not just a competitive advantage but a necessity.