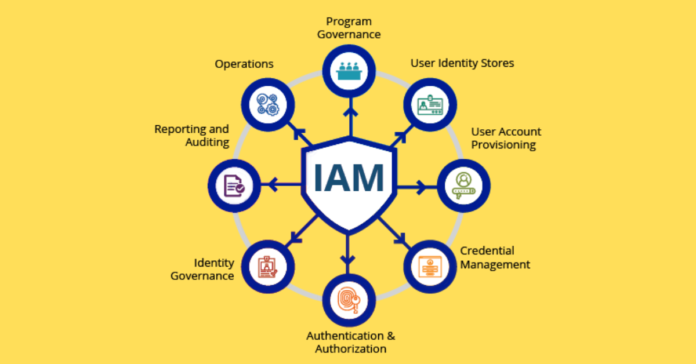
Identity and Access Management (IAM) is a critical component of organizational security and efficiency in the current digital landscape. With the prevalence of data breaches and cyber threats, the implementation of robust IAM systems has become a necessity for businesses of all sizes. This article delves into the fundamentals of IAM, its significance, implementation strategies, and technological aspects, and also explores the future of IAM in the context of evolving cybersecurity threats and technological advancements.
The Significance of IAM
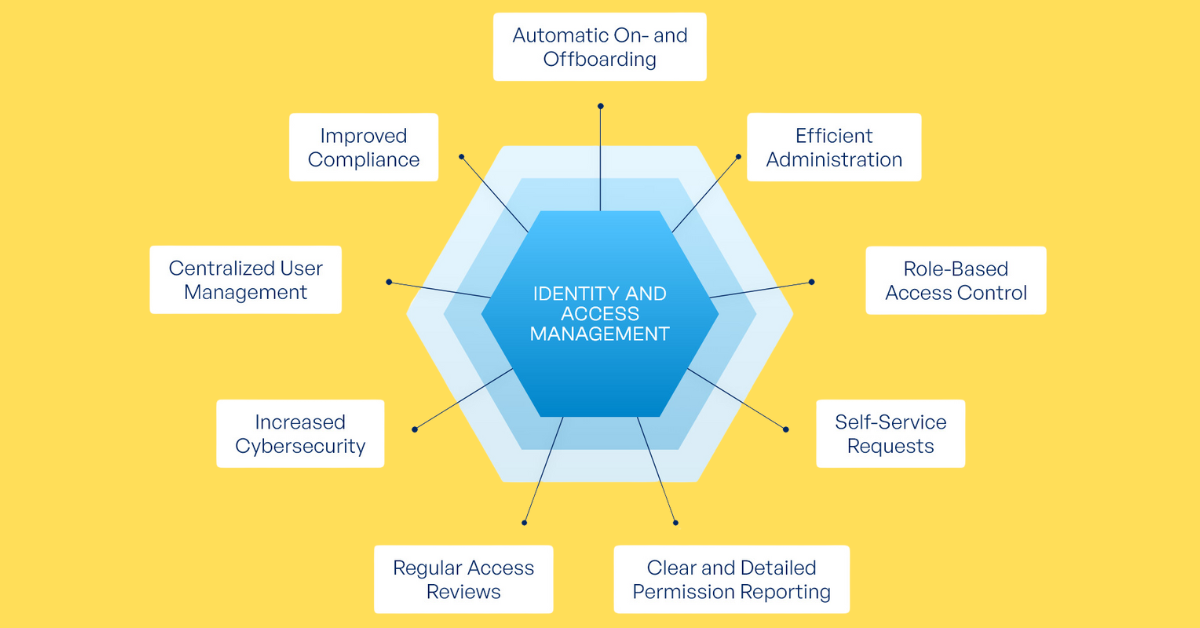
IAM ensures that the right individuals within an organization have access to the necessary resources and tools to perform their roles effectively. By managing user identities and access levels, IAM systems streamline the process of granting and revoking access, thereby enhancing both security and productivity. Moreover, IAM technologies allow businesses to extend network access to users outside the organization, such as customers, partners, contractors, and suppliers, without compromising security. This facilitates better collaboration, enhanced productivity, increased efficiency, and reduced operating costs, providing a competitive advantage to businesses.
IAM and Regulatory Compliance
In addition to bolstering security measures, IAM also plays a critical role in regulatory compliance. With data protection standards such as GDPR and HIPAA imposing strict requirements on organizations regarding data security, IAM solutions provide the necessary framework to adhere to these regulations seamlessly. IAM systems also generate compliance reports and enforce access controls, further facilitating regulatory compliance.
Functionality of IAM
IAM systems offer a range of functionalities aimed at managing user identities, provisioning and de-provisioning access, authenticating users, authorizing access levels, generating reports, and enabling single sign-on capabilities. These features collectively contribute to a comprehensive approach to identity and access management. Single sign-on (SSO) is an authentication scheme that enables users to log in once and gain secure access to multiple related applications and services, saving time and limiting losses.
IAM Authentication and Authorization
Authentication involves verifying the identity of users, software, or hardware accessing the system, while authorization determines the specific level and type of access granted to each entity. IAM systems employ various authentication methods, including multi-factor authentication (MFA), to ensure robust security measures. MFA is an identity verification method wherein a user must supply at least two pieces of evidence to prove their identity, enhancing the security of the authentication process.
Difference Between Identity Management and Access Management
While identity management focuses on confirming the identity of individuals and storing relevant information, access management dictates the resources and permissions granted to authenticated users. IAM systems integrate both aspects to establish a cohesive security framework. This integration is crucial in the face of sophisticated threat landscapes, where common attack vectors include stolen credentials and brute forcing.
Cloud vs. On-Premises IAM
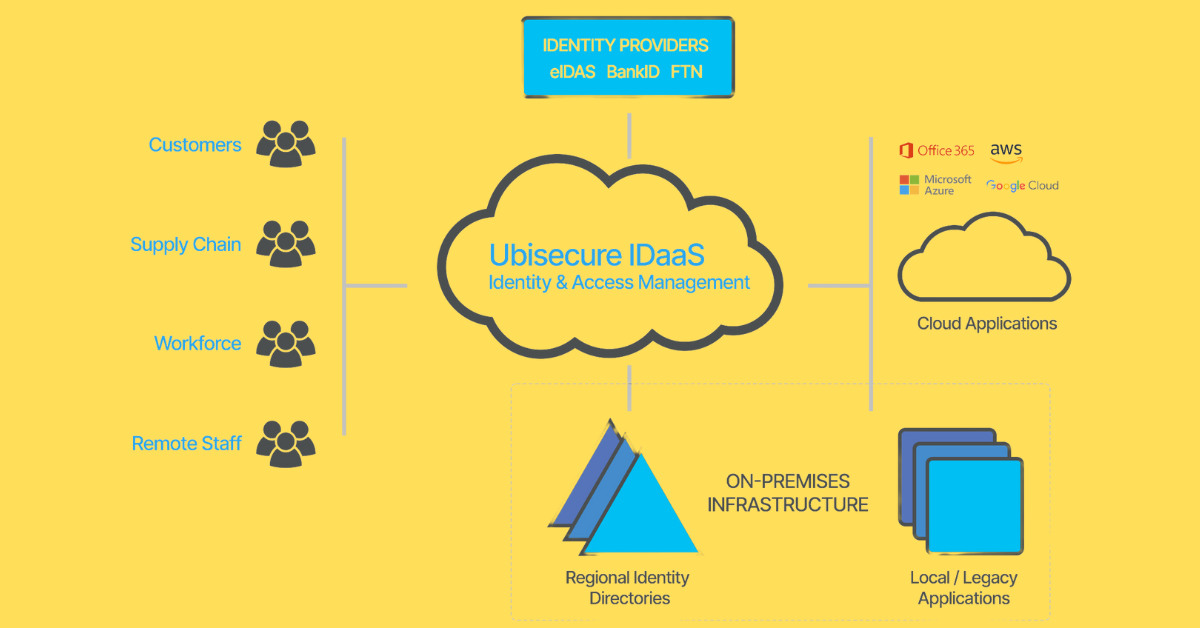
Traditionally, IAM solutions were deployed on-premises, requiring physical infrastructure and maintenance. However, the shift towards cloud-based IAM services offers greater flexibility, scalability, and cost-effectiveness for organizations, eliminating the need for extensive in-house resources. This shift has been particularly significant in the context of increasing remote work and cloud adoption trends, as well as the rise in ransomware and phishing attacks related to the COVID-19 pandemic.
AWS Identity and Access Management
Amazon Web Services (AWS) offers a comprehensive IAM service, allowing organizations to manage user access to AWS resources efficiently. With features such as fine-grained access control, multi-factor authentication, and integration capabilities, AWS IAM enhances cloud security for businesses.
Tools Required for IAM Implementation
Implementing IAM necessitates various tools, including password management software, provisioning applications, security policy enforcement tools, and identity repositories. These tools enable organizations to establish robust identity and access management frameworks tailored to their specific requirements.
IAM Implementation Strategy
An effective IAM implementation strategy encompasses centralized identity management, secure access protocols, policy-based control mechanisms, zero-trust policies, secured privileged account management, and comprehensive training and support initiatives.
Zero-Trust Policy in IAM
Zero-trust principles, such as least-privilege access and identity-based security policies, form the foundation of modern IAM frameworks. By continuously monitoring and securing user identities and access points, organizations can mitigate security risks effectively.
Secured Privileged Accounts in IAM
Privileged accounts, which hold significant access rights within IAM systems, require enhanced security measures to prevent unauthorized access and potential breaches. Implementing strict controls and monitoring mechanisms for privileged accounts is essential for maintaining overall system integrity.
Training and Support in IAM
User training and ongoing support are vital components of successful IAM implementations. Ensuring that employees understand IAM policies, best practices, and security protocols minimizes the risk of inadvertent security breaches and fosters a culture of security awareness within the organization.
IAM Technologies
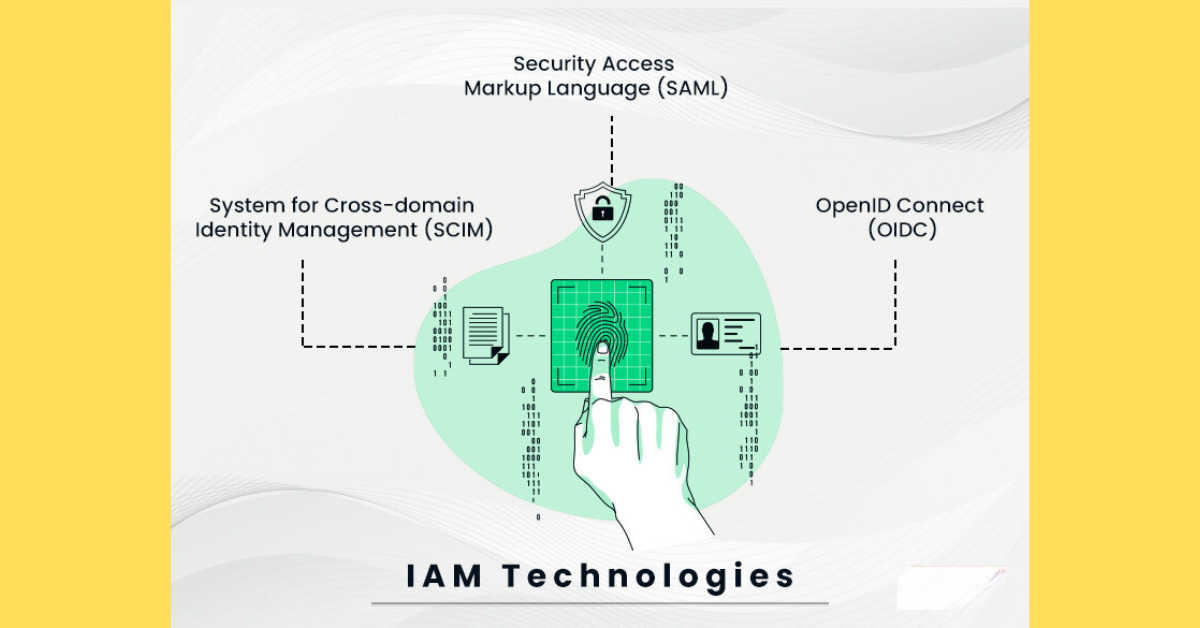
IAM systems leverage various technologies and standards, including Security Assertion Markup Language (SAML), OpenID Connect (OIDC), and System for Cross-domain Identity Management (SCIM), to facilitate seamless authentication, authorization, and user provisioning processes.
The Future of IAM
As cybersecurity threats evolve and technology advances, IAM systems are expected to incorporate more sophisticated features and capabilities. These may include elements of biometrics, machine learning, artificial intelligence, and risk-based authentication. The future of IAM also lies in the ability to flexibly deploy access control measures, define security policies, and assign specific actions according to users’ attributes and role-based access control on the fly. This will allow security administrators to maintain better control over user requests and offer efficient fine-grained policy enforcement.
Conclusion
Identity and Access Management (IAM) is an indispensable aspect of modern cybersecurity and organizational efficiency. By implementing robust IAM solutions, businesses can enhance security, streamline access management processes, and ensure regulatory compliance effectively. As we move forward, the importance of IAM will only continue to grow, making it a vital area of focus for organizations aiming to secure their digital assets and optimize their operations.
FAQs:
What are the primary objectives of Identity and Access Management (IAM)?
IAM aims to ensure secure access to organizational resources while enhancing productivity by efficiently managing user identities and access levels.
How does IAM contribute to regulatory compliance?
IAM solutions facilitate compliance with data protection standards by implementing stringent security measures, generating compliance reports, and enforcing access controls.
What role does multi-factor authentication (MFA) play in IAM?
MFA enhances authentication security by requiring users to provide multiple forms of verification, such as passwords, biometrics, or physical tokens, thereby reducing the risk of unauthorized access.
Why is user training essential in IAM implementations?
User training helps employees understand IAM policies, security protocols, and best practices, reducing the likelihood of security breaches due to human error or negligence.
What are some common IAM technologies used in modern systems?
IAM systems often leverage technologies such as SAML, OIDC, and SCIM to facilitate secure authentication, authorization, and user provisioning processes.