Nowadays, the cyber threat landscape looms large, presenting a multifaceted array of risks and vulnerabilities. As technology becomes more ingrained in our daily lives, from personal interactions to critical infrastructure systems, the potential for cyberattacks to disrupt and cause harm grows exponentially. Understanding this landscape is paramount for individuals, organizations, and societies alike to fortify themselves against potential cyber onslaughts. In this article, we will delve into what constitutes the cyber threat landscape, explore recent case studies, and discuss essential components and mitigation strategies to bolster our cyber defences.
Deciphering the Cyber Threat Landscape

Basically, the cyber threat landscape represents the whole wide world of possible cybersecurity risks and alert dangers that are being experienced online. It is conceived as an ever-changing environment rather than a static construct that reacts to technological developments and the enemy’s ever-changing strategies. This domain entails a myriad of threats, vulnerabilities, and actors, which implies that each of them encompasses particular problems related to the safety of digital assets. From solo hackers who seek monetary gain to countries competing in the international arena by means of espionage use and destruction, the reasons behind cyber threats are diverse and variable.
Distinguishing the complexity of this terrain is of primary importance for creating cybersecurity frameworks that would take into account different sectors and characteristic features of specific threats. As an illustration, the money system could be faced with problems such as fraud and taking assets by force. In contrast, the energy industry could face challenges like disturbances in critical activities. The other aspect of cyber security is that health services might be subject to deliberate attacks that are committed to compromise sensitive information about patients or to undermine vital services. Cybersecurity risks are always sector-dependent, and thus, when different organizations recognize this fact, they can prioritize their cybersecurity efforts and allocate resources effectively.
Case Study: Colonial Pipeline Ransomware Incident
The Colonial Pipeline ransomware malware attack is an eye-opener to the chaos that dwells in the cyber threat environment. In May 2021, it was the energy pipeline operator’s turn to crash into a ransomware attack engineered by the notorious DarkSide hackers. The attack resulted in a scheduled temporary shutdown of the pipeline, resulting in fuel disruption nationwide along the East Coast, thus having an offal effect on the economy.
The criminals, using a VPN account obtained illicitly in Eastern Europe, infiltrated Colonial Pipeline’s network. Subsequently, they made use of “ransomware” that encompassed crucial systems and data while asking for a hefty payoff in exchange for decryption keys. The company Colonial Pipeline, faced with a potential long-term failure and an infinite growth of the losses in the economy, as a result, decided to pay the ransom – almost millions of dollars, to speed up the return of the operations.
The Colonial Pipeline case has shown the persistent vulnerabilities among critical infrastructures and their shared dependence on a highly interconnected economy. Moreover, this incident exposes the ever-shifting techniques with which the ransomware attackers operate and the evolution of their monetary incentives. They are becoming progressively professionalized and sophisticated in their attacks. The event is a dire warning in terms of sectors, and organizations in all sectors should improve their cyber resilience and ensure readiness for cyber events.
Essential Components of the Cyber Threat Landscape

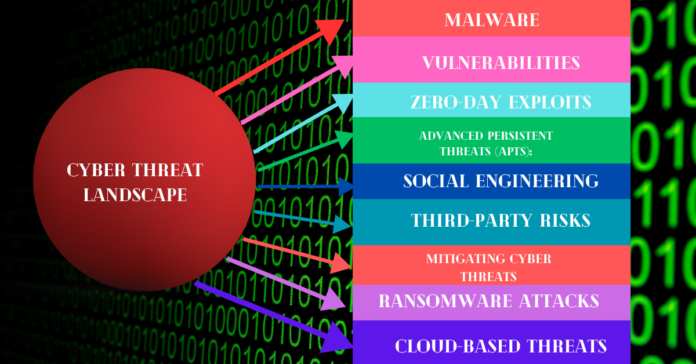
To grasp the intricacies of the cyber threat landscape, it’s imperative to delineate its key constituents. These components include:
Threat Actors: Spanning a spectrum from individual hackers to nation-state-sponsored cyber warfare units, the landscape teems with diverse adversaries, each wielding distinct motivations and capabilities. State-sponsored hackers may target government agencies or critical infrastructure for political or economic gain. At the same time, criminal syndicates focus on financial exploitation through activities such as ransomware attacks and data theft.
Attack Vectors: Encompassing a wide range of techniques and tactics, attack vectors are the conduits through which adversaries breach defenses and compromise systems. Common attack vectors include phishing emails, malicious software (malware), social engineering tactics, and exploiting vulnerabilities in software or hardware components.
Malware: From viruses and worms to Trojans and botnets, the proliferation of malicious software poses a pervasive threat to digital infrastructure and data security. Malware can be used to gain unauthorized access to systems, steal sensitive information, disrupt operations, or facilitate further cyberattacks.
Vulnerabilities: The cyber threat landscape teems with vulnerabilities permeating software, hardware, and network infrastructure. These vulnerabilities provide fertile ground for exploitation by threat actors seeking to infiltrate systems and wreak havoc. Vulnerabilities can arise from coding errors, misconfigurations, or outdated software versions, among other factors.
Zero-Day Exploits: These undisclosed vulnerabilities represent a potent weapon in adversaries’ arsenals, enabling stealthy incursions into unpatched systems and circumventing conventional security measures. Zero-day exploits are particularly challenging for defenders as there are no known patches or fixes available to mitigate the risk.
Advanced Persistent Threats (APTs): Characterized by stealthy, long-term operations orchestrated by state-sponsored actors, APTs pose a formidable challenge to cybersecurity. These adversaries often target critical infrastructure, government agencies, or organizations with valuable intellectual property, using sophisticated tactics to maintain persistent access and exfiltrate sensitive data.
Social Engineering: Leveraging psychological manipulation, social engineering tactics entice unwitting individuals into divulging sensitive information or unwittingly facilitating cyber intrusions. Standard social engineering techniques include pretexting, phishing, and baiting, all of which exploit human psychology and trust to achieve malicious objectives.
Third-Party Risks: Collaboration with external vendors and partners introduces additional vectors of vulnerability into organizational networks and supply chains. Third-party risks can arise from lax security practices, inadequate oversight, or compromised credentials, highlighting the importance of stringent vendor management and robust security protocols.
Mitigating Cyber Threats: Navigating Current Trends
Against the backdrop of a rapidly evolving cyber threat landscape, it’s imperative to stay abreast of emerging trends and deploy proactive measures to mitigate potential risks. Key trends shaping the current cybersecurity landscape include:
Ransomware Attacks: The proliferation of ransomware-as-a-service (RaaS) models underscores the escalating threat posed by ransomware, which has become a lucrative business for cybercriminals. Ransomware attacks target organizations of all sizes and sectors, encrypting critical data and demanding ransom payments in exchange for decryption keys. To defend against ransomware attacks, organizations must implement robust incident response plans, maintain up-to-date backups, and invest in cybersecurity awareness training for employees.
Cloud-Based Threats: As organizations increasingly migrate to cloud-based infrastructure, the spectre of misconfigurations, data breaches, and unauthorized access looms large. Cloud service providers offer robust security features, but the shared responsibility model dictates that organizations are responsible for securing their data and applications. To mitigate cloud-based threats, organizations must implement stringent security controls, conduct regular risk assessments, and leverage security-as-a-service solutions to monitor and protect cloud environments.
IoT Vulnerabilities: The burgeoning adoption of Internet of Things (IoT) devices amplifies the risk landscape, as these interconnected devices often lack robust security features and are vulnerable to exploitation. IoT devices such as smart thermostats, security cameras, and industrial sensors can be hijacked and used to launch DDoS attacks, exfiltrate sensitive data, or compromise network integrity. To mitigate IoT vulnerabilities, organizations must implement robust authentication mechanisms, segment IoT devices from critical network assets, and apply regular firmware updates to address security vulnerabilities.
Social Engineering and Phishing: Persistent threats such as phishing emails and social engineering scams underscore the critical need for heightened cybersecurity awareness and multifactor authentication to fortify defences against human-centric exploits. Cybercriminals leverage social engineering tactics to manipulate individuals into divulging sensitive information or unwittingly facilitating cyber intrusions, highlighting the importance of ongoing cybersecurity training and education programs for employees.
Deepfake Technology: The proliferation of deepfake technology underscores the imperative for enhanced media literacy and advanced detection mechanisms to combat the dissemination of manipulated audiovisual content. Deepfake technology uses artificial intelligence algorithms to create highly realistic but fabricated images, videos, and audio recordings, which can be used to spread misinformation, defame individuals, or undermine trust in public institutions. To counter the threat posed by deepfakes, organizations must invest in media literacy education, develop robust authentication mechanisms for verifying content authenticity, and deploy advanced detection tools capable of identifying manipulated media.
Conclusion
Comprehending the nuances of the cyber threat landscape is indispensable for devising robust cybersecurity strategies capable of withstanding the ever-evolving array of digital perils. By remaining vigilant, proactive, and adaptive, individuals and organizations can navigate this treacherous terrain and safeguard their digital assets against potential cyber incursions.
FAQs
What is the cyber threat landscape, and why is it important?
The cyber threat landscape refers to the various risks and threats in the digital world. Understanding it helps develop effective strategies to protect against cyberattacks.
What are the critical components of the cyber threat landscape?
Key components include threat actors, attack vectors, malware, vulnerabilities, zero-day exploits, APTs, social engineering, and third-party risks.
How can organizations mitigate cyber threats?
Strategies include staying informed, deploying robust security measures, conducting audits, and providing cybersecurity training.
What are current trends in the cyber threat landscape?
Trends include ransomware attacks, cloud-based threats, IoT vulnerabilities, social engineering, and deepfake technology.
How can individuals protect themselves against cyber threats?
Use strong passwords, enable two-factor authentication, be cautious of suspicious emails/links, keep software/devices updated, and stay informed about cybersecurity best practices.