Imagine a world without restrictions on your doors or accounts. All sounds a little frightening, correct? That’s the place where cyber security is involved. It’s similar to a digital shield that protects our computers, networks, and data from intruders who might want to cause harm. These troublemakers, who are often referred to as hackers, are individuals or groups of individuals that are intended to steal information or disrupt our digital lives.
Cyber security is the science of preventing digital intrusion into systems, networks, and computers. These cyberattacks are typically intended to access, alter, or destroy crucial information, take money from users, or disrupt normal business processes. In general, cyber security is similar to a shield that safeguards your computer and data from hackers or criminals, just like a conventional shield does to a knight!
Types of Cybersecurity Threats
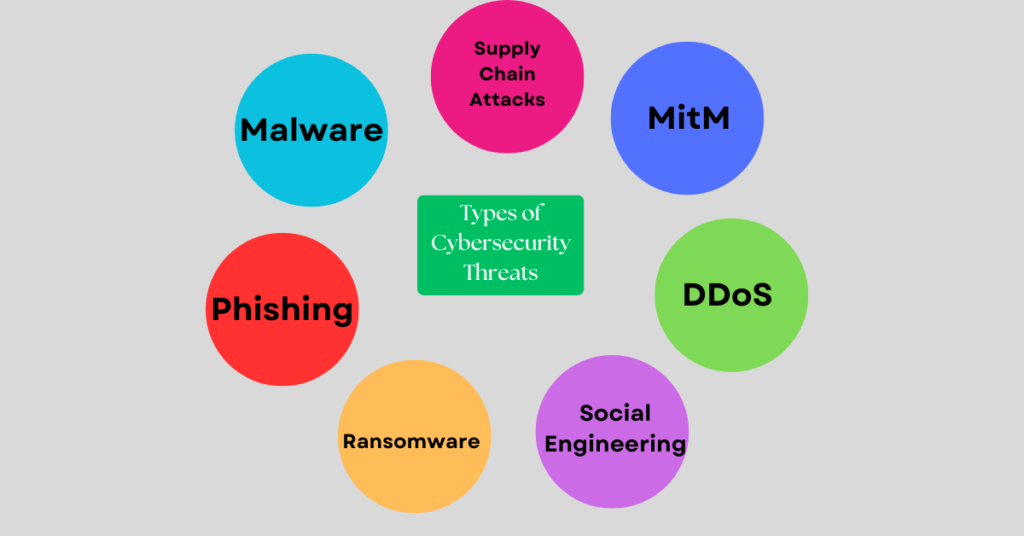
Cybersecurity threats come in different shapes and sizes. Here are some common types:
- Malware: Consider this as the general cold of the digital world. It’s malicious software that is intended to cause damage or prevent computers from functioning. Examples include viruses, worms, and ransomware. Remember that your computer became sluggish, or unable to open specific files? That could have been considered malware!
- Phishing: Imagine a message that is apparently coming from your bank and telling you to update your account details. You click the link and, in a state of unawareness, type in your personal information, just to later realize that it was a bogus site that was actually meant to snatch your data. This is known as phishing, where people are misled into thinking that someone is trustworthy through their deception tactics.
- Ransomware: This harmful piece of software is similar to a digital abductor. It’ll seal your data or system into a state that’s difficult to get out of, until you pay a fee. Imagine not having the ability to access your essential school endeavors or your family’s photos! This is why it’s important to have strong passwords and to backup your information on a regular basis.
- Social Engineering: It’s less about technical tricks and more about human communication that poses the threat here. It is the action of turning people to make them share private information or perform certain actions. For instance, the wrongdoer in question could act as a tech support rep on a fake basis and make you believe them by then acquiring the connection to your computer.
- Distributed Denial of Service (DDoS) Attacks: Imagine your favorite online game that you have been playing for a while is suddenly out of commission and you can’t play it. Such a scheme is likely to be a DDoS attack, which is a type of cybercrime in which a network receives more traffic than the server can handle. The result is the unavailability of its intended users. Basically, it is the same as an extensive crowd blocking the entrance to a store, so that normal customers can’t enter the shop.
- Man-in-the-Middle (MitM) Attacks: Visualize yourself mailing a postcard to your friend, but a stranger picks it up, skims through it, and possibly even tampers with it before delivering it to your concerned friend. This is similar to a MitM attack, it is an attack where the attacker intercepts and alters the communication between two parties without their knowledge.
- Supply Chain Attacks: Imagine purchasing a new mobile phone, and after some time, you notice that it has surveillance software. This is a supply chain attack, a technique, using which hackers strike at software developers and vendors to cause damage using legal applications and distributing malware.
What is Cyber Security in Simple Words?
Cybersecurity is the step of keeping your computer, network, and data free from illegal access, attacks, or damage. Imagine it as a digital version of a life and death sword. This shield acts as a barrier that protects your data from being accessed by hackers and other online threats, and is the actual real-time safety measure for a computer.
7 Layers of Cyber Security
Think of cyber security as a castle with multiple layers of defense:
- Network Security: The outer walls and moats guarding computer networks against the intruders, whether wired or wireless (Wi-Fi) ones.
- Application Security: The guards inside the castle geared towards the safety of software and devices. In particular, they are at the application level to avoid data or code within the app from being stolen or hijacked.
- Information Security: The royal treasury and the way by safeguarding the data were the ways to prevent the problems of it during storage and transmission.
- Cloud Security: The sky fortress, an iron dome that keeps threats away from data, applications, and infrastructure in the cloud.
- Mobile Security: The knights riding on horseback who are ensuring the security of mobile devices including smartphones and tablets against malware.
- Endpoint Security: The foot soldiers, who are keeping the individual computers and smartphones from connecting to the network at all costs, are the ones who are relying on.
- Internet of Things (IoT) Security: These days the threats to networks and devices connected to the internet are very high, especially if we are talking about smart home gadgets and industrial machines.
How Does Cyber Security Work?
Cyber security works like a complex security system with different components working together:
- Firewalls: At the same time being a fortress that divides trusted and untrusted networks is as convenient as a doorman who allows only certain people inside the country’s borders.
- Antivirus Software: It plays no role in the situation of spreading malware, and also it is the software that does not have to be righteous for giving a type of training or learning as to how to charge an enemy slowly.
- Encryption: This turns the data into the encryption method to avoid the unauthorized entrance, and that is exactly the meaning of the invisible ink encryption method where a secret message is hidden in a normal looking text piece without an actual ink but in such a way that the recipient can read the message clearly.
- Multi-Factor Authentication (MFA): For example, an event where the user has to confirm a suggestion in order to get the needed information or that the server itself has a secure connection and then the client or user is authenticated with a password.
- Security Awareness Training: It highlights them on the potential risks, as much as on the other hand prepares them for the right actions, for example, in this case the dwellers are properly trained to recognize and inform them about any suspect or dangerous activity.
Is Cyber Security a Good Career?
Absolutely! Since technology is more and more significant, the demand for highly qualified cybersecurity professionals is at an all-time high. Isn’t it just amazing to be a digital superhero in an interconnected world, saving it from hacking? Information Technology jobs in cybersecurity give out very high salaries with job security and room for growth. And it’s still a developing area, so you will never be a person who will sit out their time and feel indifferent.
Why is Cyber Security Important?
Nowadays, cyber security is more demanding than ever. Here’s why:
- Protecting Sensitive Data: It provides the personal and organizational information in such a way that is confidential and safe, as it were for important documents if they were in a vault.
- Preventing Cyber Attacks: It acts as a shield to keep away from all sorts of cyber risks, which can damage us online.
- Safeguarding Critical Infrastructure: It protects vital services such as power grids and water systems from cyber threats, thus meeting our primary needs.
- Maintaining Business Continuity: It ensures that enterprises can still be involved in the process of continuing their operations without being invaded by the cyber-attacks, hence avoiding potential interruptions and financial losses.
- Compliance with Regulations: This mechanism helps companies in meeting the legal terms of data protection so that they do not get serious fines and court cases.
- Protecting National Security: It is the fact that cyber-attacks are not able to occur and the country’s security may not be put in danger, which ensures the people’s safety.
- Preserving Privacy: It makes sure that personal data is being kept confidential and secure, which ultimately preserves the citizens’ right to privacy on the internet.
Be Cyber Smart!
Cybersecurity is the responsibility of everyone. Through learning the fundamentals and observing safe online practices, we can all play a part in making the digital world more secure. First of all, it is better to !Remember to create strong passwords, be cautious of any suspicious emails and links, and upgrade your software to the latest version etc. Stay alert and try to find out the newest threats. The means to secure you should also be introduced.


